In a digital world where data is the new gold, securing this precious asset has become increasingly paramount. A recent event puts this into stark perspective: the data breach at 23andMe, a popular direct-to-consumer genetic testing company. This breach compromised the DNA data of an astonishing 6.9 million users, marking a significant milestone in the annals of cyber-attacks.

The Anatomy of the Data Breach
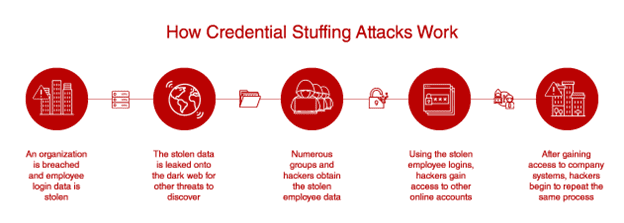
The hackers exploited a common vulnerability known as a “credential stuffing attack”.
The “credential stuffing attack” is a method used by cybercriminals that takes advantage of users who reuse their usernames and passwords across multiple accounts. The attackers compile lists of usernames and passwords from previous data breaches and use these to attempt to gain access to other accounts. This automated process can be executed on a large scale, affecting thousands or even millions of users at once.
In the case of 23andMe, the culprits targeted the DNA Relatives feature, which connects users with potential relatives based on their genetic data.
This incident highlights the inherent risks in using the same login credentials across multiple platforms and the importance of taking proactive steps to secure your online accounts. It’s a stark reminder that in the digital age, personal information isn’t just about names and addresses, but can extend to biological data as well. With such data falling into the wrong hands, the implications can be far-reaching and potentially devastating.
How to Defend Against This Threat – Password Managers
So, how can you avoid falling victim to such attacks? One effective solution is using a password manager. Password managers store all your passwords in a secure vault, encrypting them to ensure they remain inaccessible to hackers.
Aside from storing and encrypting your passwords, password managers offer several other key benefits that can bolster your online security. Firstly, they help eliminate the bad habit of password reuse. Since the manager creates a unique password for each of your accounts, the risk of multiple accounts being compromised from one data breach is significantly reduced.
Secondly, password managers often have built-in password generators that create long, complex passwords which are harder for hackers to crack. These passwords typically include a combination of uppercase and lowercase letters, numbers, and special characters, making them far more secure than common, easily guessable passwords.
Moreover, most password managers also have an autofill feature that can fill in your username and password automatically when you visit a site. This not only saves you time but also protects you against keylogging attacks, where hackers record your keystrokes to capture your login credentials.
Lastly, some password managers even provide a security audit, alerting you to weak or duplicate passwords, and prompting you to update them. They may also notify you if any of your accounts have been involved in a recent data breach.
In essence, using a password manager is like having a personal bodyguard for your digital life. It’s an essential tool in the fight against cyber threats, helping to keep your online identity safe and secure.

How to Defend Against This Threat – Passwords
While password managers greatly assist in creating and storing secure passwords, it’s crucial not to become complacent. Regularly updating your passwords is a key step in maintaining your online security. This is because, even with strong, complex passwords, there’s always a risk of them being exposed in a data breach.
Updating your passwords every three months might seem like a daunting task, especially if you have multiple online accounts. However, this is where a password manager can prove invaluable, as it can automate the process, saving you time and effort. Some password managers even have built-in reminders to notify you when it’s time to update your passwords.
In addition to regularly updating your passwords, it’s also important to be aware of common phishing techniques used by cybercriminals to steal login credentials. This includes being cautious of suspicious emails or messages that ask for personal information or prompt you to click on a link.
Furthermore, enabling multi-factor authentication (MFA) whenever it’s available can add an extra layer of security to your accounts. MFA requires you to provide two or more pieces of evidence to verify your identity when logging in, making it significantly more difficult for attackers to gain unauthorized access.

How to Defend Against This Threat – Wi-Fi Networks
Public Wi-Fi networks, such as those found in cafes, airports, or hotels, though convenient, are not always secure. Cybercriminals can easily exploit these networks to gain unauthorized access to your devices and steal sensitive information. Therefore, it’s crucial to be mindful of the networks you connect to, especially when accessing or transmitting sensitive data.
One way to enhance your security on public Wi-Fi networks is by using a SASE (Secure Access Service Edge) pronounced ‘sassy’ solution. SASE solutions bundles network and security functions into a single platform. It provides many services including encryption of your internet connection, making it harder for hackers to intercept and decipher your data. It creates a secure wide area network for your data to travel through, protecting it from potential eavesdroppers on public networks.
In essence, while the convenience of public Wi-Fi can be enticing, it’s important to take steps to safeguard your online activities. By combining secure practices like using a SASE solution maintaining updated software, and enabling firewalls, you can significantly reduce the risk of falling victim to cyber-attacks.

Wrap Up
The 23andMe data breach underscores the vulnerability of our personal information in the digital age. It highlights that no organization, regardless of its size or reputation, is immune to cyber threats. As such, we must be proactive in protecting our data and not solely rely on companies to do so.
A key step towards securing our online presence is by embracing password managers. These tools not only help us create complex passwords that are hard for hackers to crack but also store them securely, so we don’t have to remember each one. They can also alert us when it’s time to change our passwords, adding another layer of protection against potential breaches.
Creating strong passwords is equally important. A robust password should include a combination of upper- and lower-case letters, numbers, and special characters. It should also be unique to each account to prevent a security breach on one account from affecting others.
Being cautious with internet connections is another crucial aspect of online security. Public Wi-Fi networks, while convenient, can expose our devices to hackers. Therefore, it’s advisable to use secure, private connections when accessing sensitive information or consider using a SASE (Secure Access Service Edge) solution for an added layer of security on public networks.
Furthermore, we should stay abreast of the latest cybersecurity trends and threats. Regularly updating our knowledge can help us identify potential risks and take appropriate measures to protect our data.
In essence, the 23andMe data breach is a wake-up call for all internet users. It emphasizes that online security is a shared responsibility. By equipping ourselves with the right tools and knowledge, we can significantly strengthen our defenses against cyber threats and safeguard our personal information.
What Are Your Next Steps
At IT Pros Management, we have a team of dedicated cyber security professionals who specialize in this field. They bring their extensive experience and expertise to help businesses across various industries. We understand that each industry has its unique set of challenges and requirements, and we tailor our cyber security services accordingly to offer the most effective solutions.
Our commitment to efficiency and reliability is reflected in our 24/7 live support and security operations center. We are always ready to respond to your needs, ensuring minimal disruption to your operations. Moreover, our strategic locations in Los Angeles County, CA; Plano, TX; Las Vegas, NV; and Orange County, CA, allow us to provide prompt and efficient service to our clients.
To learn more about IT Pros Management services and solutions and how they can help your business or non-profit grow and scale visit their website at Los Angeles IT Services | IT Services Los Angeles | IT Pros (itprosmanagement.com) or call them at (866) 487-7671.
Contact
IT Pros Management
303 N. Glenoaks Blvd Suite 200 Burbank, Ca 91502
(866) 487-7671
www.itprosmanagement.com
And remember, with IT Pros Management you can RELAX! I.T. is Covered

