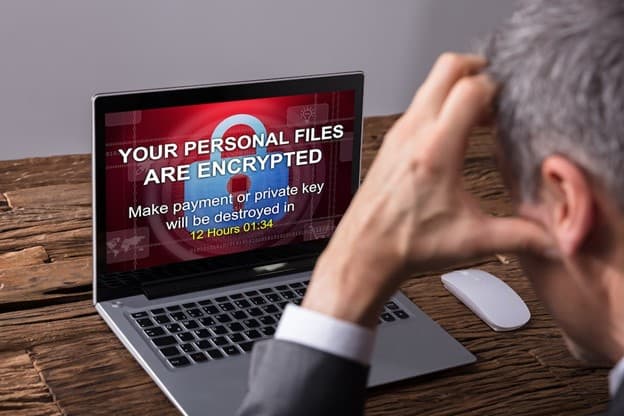
As a business owner, whether you’re steering a startup or managing a mid-size enterprise, understanding the digital threats that loom over the corporate world is more crucial than ever. The United States, a beacon of technological advancement and innovation, has paradoxically become a prime target for cybercriminals, with ransomware attacks at the forefront of these digital threats.
In 2023, nearly half of all ransomware incidents were aimed at organizations within North America, signaling a stark reminder of the risks that lie in our increasingly digital operations. This article aims to provide a comprehensive overview of ransomware, including its implications for businesses, preventative measures, and response strategies, with a keen eye on projected statistics for 2024 and the specific impact on small to mid-size businesses.

Understanding Ransomware
Ransomware is a type of malicious software designed to block access to a computer system or data, typically by encrypting files, until a sum of money is paid. This digital extortion has become a lucrative venture for cybercriminals, targeting entities of all sizes across various sectors. The modus operandi involves exploiting vulnerabilities within network security, phishing emails, or software exploits to gain access and deploy ransomware. Once the data is encrypted, the attackers demand a ransom, often in cryptocurrency, for the decryption key. The immediacy and anonymity of these transactions make it a preferred method for attackers, placing immense pressure on the affected organizations.

The 2024 Outlook
As we venture into 2024, the forecast for ransomware attacks in the U.S. is grim. Cybersecurity experts predict an uptick in the frequency and sophistication of these attacks, with small to mid-size businesses increasingly in the crosshairs. The reasons are multifaceted: smaller businesses often lack the robust cybersecurity infrastructure of larger corporations and are perceived as having a higher likelihood of paying the ransom to quickly restore operations. This vulnerability presents a significant risk, not just in terms of financial loss, but also regarding data privacy, operational integrity, and brand trust.

Mitigating Risks: Prevention and Proactivity
Strengthening Cybersecurity Posture
The first line of defense against ransomware is a strong cybersecurity posture. This includes regular updates to software and systems, the use of antivirus and anti-ransomware tools, and secure backups of critical data. Educating employees on the dangers of phishing emails and the importance of secure password practices is also vital, as human error remains a leading cause of security breaches.

Cyber Hygiene and Regular Audits
Maintaining good cyber hygiene through regular security audits and vulnerability assessments can identify and rectify potential entry points for cybercriminals. Employing services like threat hunting and penetration testing can further bolster your defenses by simulating attacks to test your system’s resilience.

Incident Response Planning
Having an incident response plan (IRP) in place is essential. This plan should outline the steps to take in the event of an attack, including isolating affected systems, communicating with stakeholders, and engaging with cybersecurity professionals to mitigate the attack’s impact and restore operations.
Despite best efforts, the possibility of falling victim to a ransomware attack remains. The response to such an incident is critical and can significantly affect the outcome for your business.
- Isolation: Immediately isolate the affected systems to prevent the spread of ransomware to interconnected devices or networks.
- Assessment: Engage cybersecurity experts to assess the scope and impact of the attack, determining whether it’s possible to decrypt files without succumbing to the ransom demands.
- Notification: Notify relevant authorities and potentially affected parties. Transparency in communication can help manage the situation’s reputational aspects.
- Recovery: Utilize backups to restore encrypted data and bring critical services back online as soon as possible
- Post-Incident Analysis: After resolving the immediate threat, conduct a thorough review of the incident to identify vulnerabilities and strengthen security measures to prevent future attacks.

Top Takeaways
- Awareness and Preparation are Key: Understanding the threat of ransomware and preparing accordingly is vital for businesses of all sizes. This includes implementing robust cybersecurity measures, educating staff, and having an effective incident response plan.
- Proactivity Over Reactivity: Regularly reviewing and updating your cybersecurity practices can significantly reduce the risk of an attack. Proactive measures, such as maintaining secure and isolated backups and conducting regular security audits, are essential components of a comprehensive defense strategy.
- Collaboration and Communication: In the event of an attack, clear and transparent communication with stakeholders, along with collaboration with cybersecurity professionals, can help manage the situation effectively. Post-incident analysis and sharing lessons learned with the wider business community can also contribute to a collective defense against future threats.
As ransomware continues to evolve, staying informed and vigilant is paramount. By fostering a culture of cybersecurity awareness, prioritizing proactive defense measures, and preparing for the worst while striving for the best, businesses can navigate the treacherous waters of digital threats with confidence.
Let’s make 2024 a year of fortified defenses, informed strategies, and resilient operations.
What are Your Next Steps
Looking for a professional and reliable cyber security partner to help your business or non-profit scale and grow in a cost effective and SECURE manner look no further than IT Pros Management.
IT Pros Management has been delivering exceptional cyber security services and IT solutions for businesses and non-profits for 10 plus years.
To learn more about IT Pros Management cyber security services and how they can help your business or non-profit navigate the dynamic threat landscape visit their website at https://www.itprosmanagement.com/security/ or call them at
(866) 487-7671.
Contact:
IT Pros Management
303 N. Glenoaks Blvd Suite 200 Burbank, Ca 91502
(866) 487-7671
www.itprosmanagement.com
And remember, with IT Pros Management you can RELAX! I.T. is Covered

